Secrets
Every app has secrets - API keys, passwords, credentials etc... Managing secrets can be a bit of a pain, so we've built secret management into Keel that is both secure and easy to to use.
For non-sensitive configuration values use environment variables.
Defining Secrets
Secrets are defined in a keelconfig.yaml file which should be in the root of your project.
secrets:
- name: MY_SECRET
- name: MY_OTHER_SECRETNames
Secrets must be named in UPPER_SNAKE_SNAKE and cannot start with the prefix KEEL_. In the keelconfig.yaml file you only provide the names of your secrets - this is enough to enable type-safe access of your secrets in your schema and your functions.
Values
For deployed environments you can set secret values in the console by going to the Secrets section in the console.
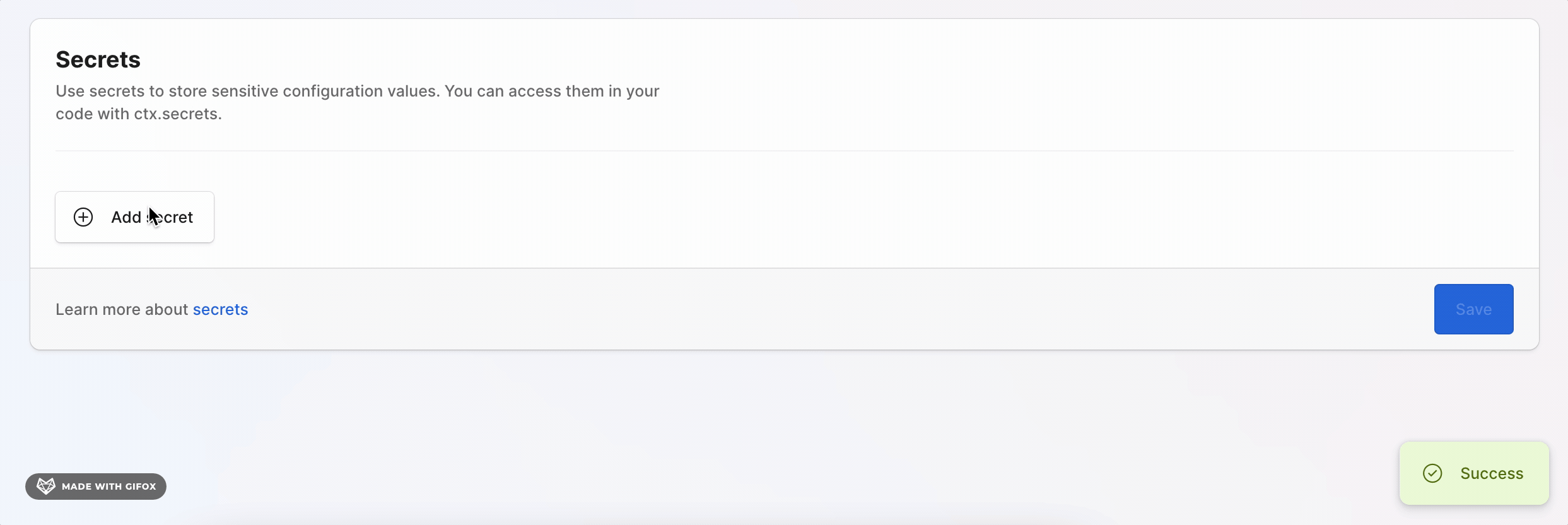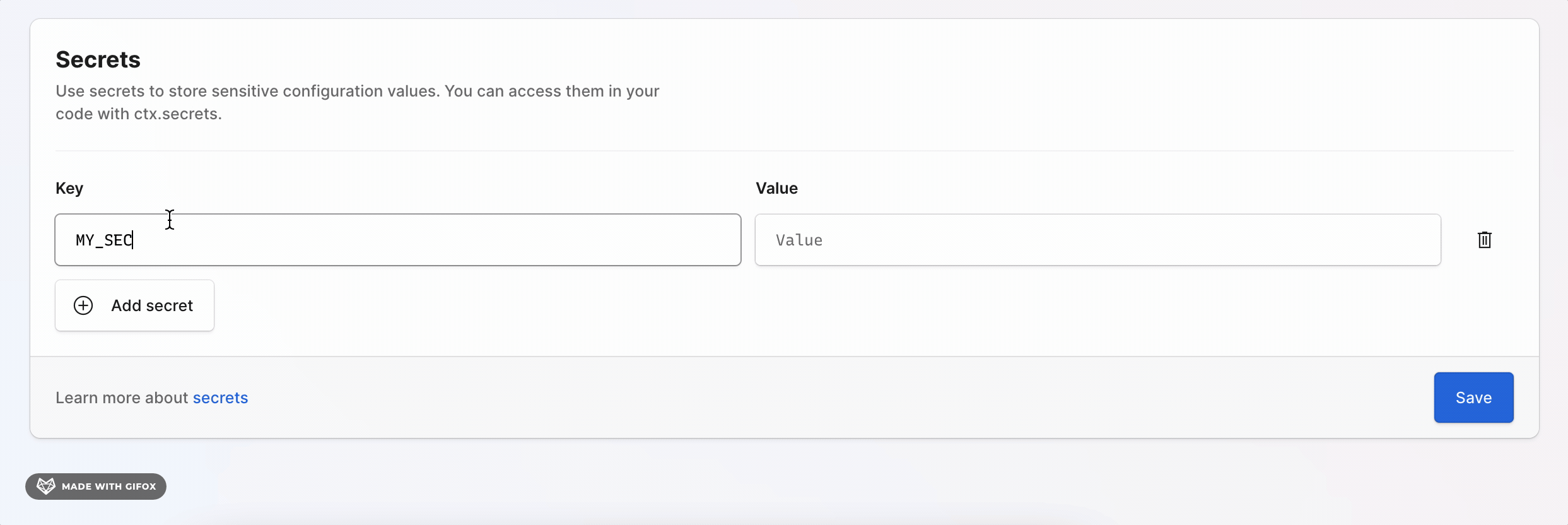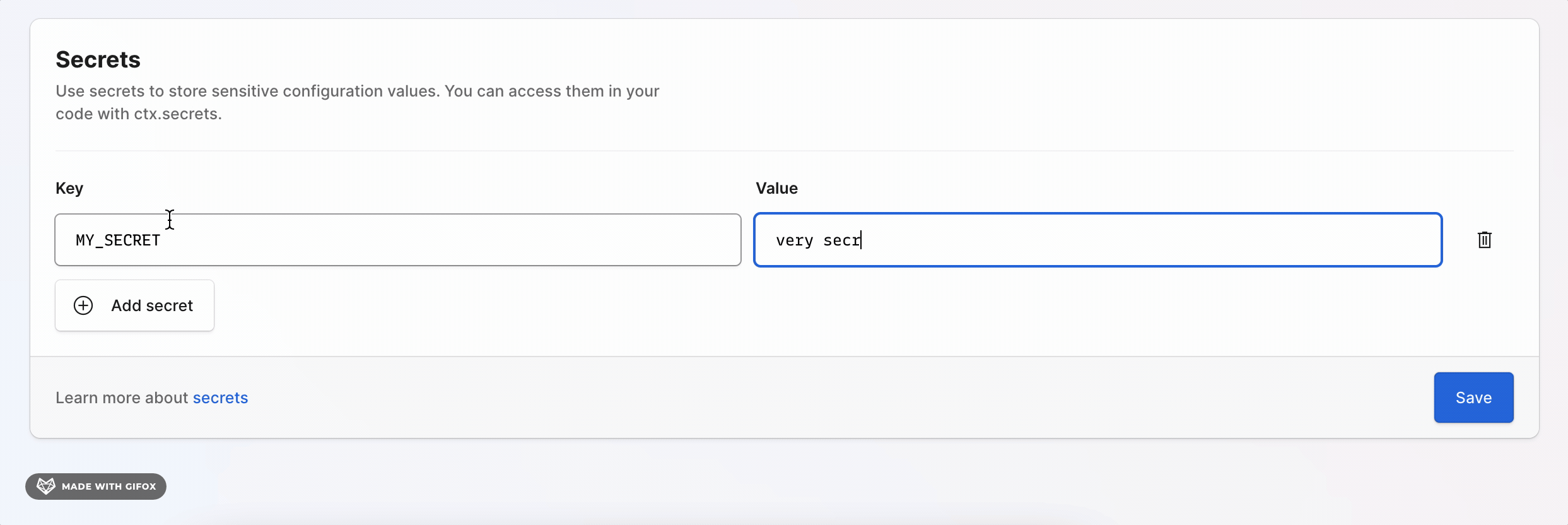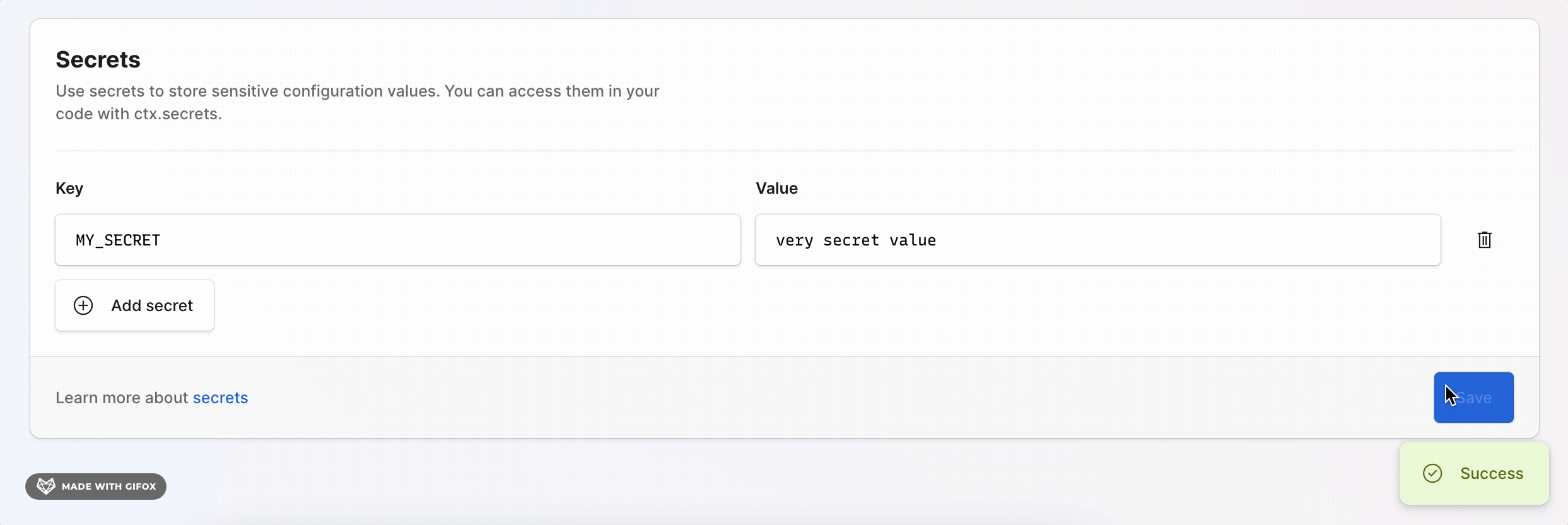
Secret values are set separately for each environment, however you don't need to set a value in every environment if you don't need to.
Using Secrets
There are two ways you will use your secrets - from your Keel schema or from your function code.
From a Keel schema
Secrets can be accessed with ctx.secrets.MY_SECRET from within any expression in your schema.
model Person {
fields {
name Text
}
@permission(
expression: ctx.headers.API_KEY == ctx.secrets.API_KEY,
actions: [get]
)
}From a function
You can access your secrets in a type-safe way through the ctx argument that is passed to your functions, for example ctx.secrets.MY_SECRET.
export default MyFunction(async (ctx, inputs) => {
// "some-vale"
ctx.env.MY_SECRET
// TypeScript will catch this with the error:
// ts(2339) Property 'FOO' does not exist on type 'Secrets'.
ctx.env.FOO
});Secrets in development
The Keel CLI comes with a set of commands that help you manage secrets in your development environment (for example when using keel run to run your app locally).
Setting secrets
To set a secret value for use in development, you can use keel secrets set. For example:
keel secrets set MY_SECRET 'my-value'Make sure to run keel generate after adding a secret, for ctx.secrets to recognise the new field
Removing secrets
To remove a secret value, you can use keel secrets remove. For example:
keel secrets remove MY_SECRETListing secrets
To view all secrets set in your development environment, you can use keel secrets list. For example:
keel secrets listTo manage secrets used in the test environment, all the CLI secrets commands will accept an env flag; e.g. keel secrets list --env test